Cybersecurity
Solutions
Reduce the risks induced by the Digital Transformation; discover our Cybersecurity solutions
Cybersecurity is a major challenge for all businesses regardless of their size or industry. Cyberattacks are becoming more frequent and more sophisticated with increasingly disasterous consequences. To protect your organisation against these threats and ensure its sustainability, it is essential to incoporate efficient cybersecurity solutions adapted to your business’ needs.
The ever-evolving digital world we live in today offers many opportunies for not only businesses, but also for cybercriminals. They know how to exploit security flaws in IT systems as well as manipulate employees to get what they want.
With impacts going well beyond business interruptions or data theft, the consequences of cyberattacks can be dramatic. Some companies are forced to close down after a cyberattack while others see their operations and image permanently altered.
In this digital era, the advent of the Cloud, remote work and the IoT, IT departments of SMBs and mid-sized companies are facing new challenges.
Get inside the
head of a hacker

Cybersecurity facts and statistics
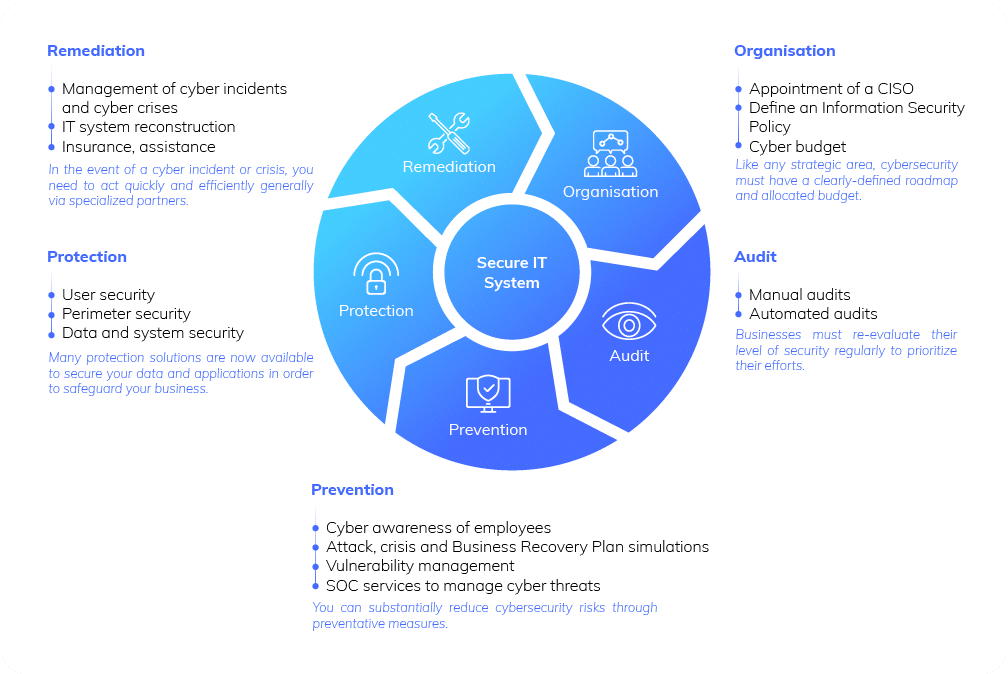
The 5 pillars of Cybersecurity
To evaluate and reduce cyber risks, companies should focus on the following areas:
Prodware Cybersecurity
solutions and services
With the digital transformation also comes the increased risk of exposed IT systems and thus more cyber threats. To help businesses manage their cyber risks, Prodware has developed a large portfolio of services from a part-time CISO (Chief Information Security Officer) to a full-time SOC (Security Operation Center) to manage your cyber risks 24/7. To complete these services, Prodware has fostered a network of strategic partnerships with top leaders in the security industry including Microsoft, which offers a vast security ecosystem for both Cloud infrastructures and On Premise.
Governance
and compliance

Part-time CISO
Provision of an experienced Chief Information Security Officer to lead your Cybersecurity strategy and ensure the integrity of your Information System against internal and external risks.

Security committee
Through regular committees, your dedicated operations manager collects and analyzes your KPIs and security incidents as part of a continuous process of improving security.

ISP (Information Security Policy) development
Define and structure the Information Security Policy for your organization.

Audit services

Infrastructure, data, collaborative tools and Dynamics software audit
Analysis of the levels of security in place and proposals of detailed action plans.

Penetration testing (ethical hacking)
Penetration tests carried out by ethical hackers to pinpoint your human and technical weaknesses so that they can be corrected.

Users and devices

Managed Services
Our Secure Workplace contract is a turnkey outsourcing service for managing your employees and your IT assets. It supports your terminals and servers, your Microsoft collaborative tools and provides all the required governance and security services to make your organization safer and more efficient.

Perimeter security

Network segmentation
Partitioning of IT assets in separate networks to limit the risks in the event of an attack.

Systems and data
Discover a few of our Cybersecurity solutions
Why choose Prodware?
Cybersecurity is a major concern for all businesses. As a digital transformation partner, Prodware also supports its customers in strengthening their cybersecurity strategy by ensuring the security of their infrastructure, professional applications, data and by offering protection services against cyber risks.